TLDR
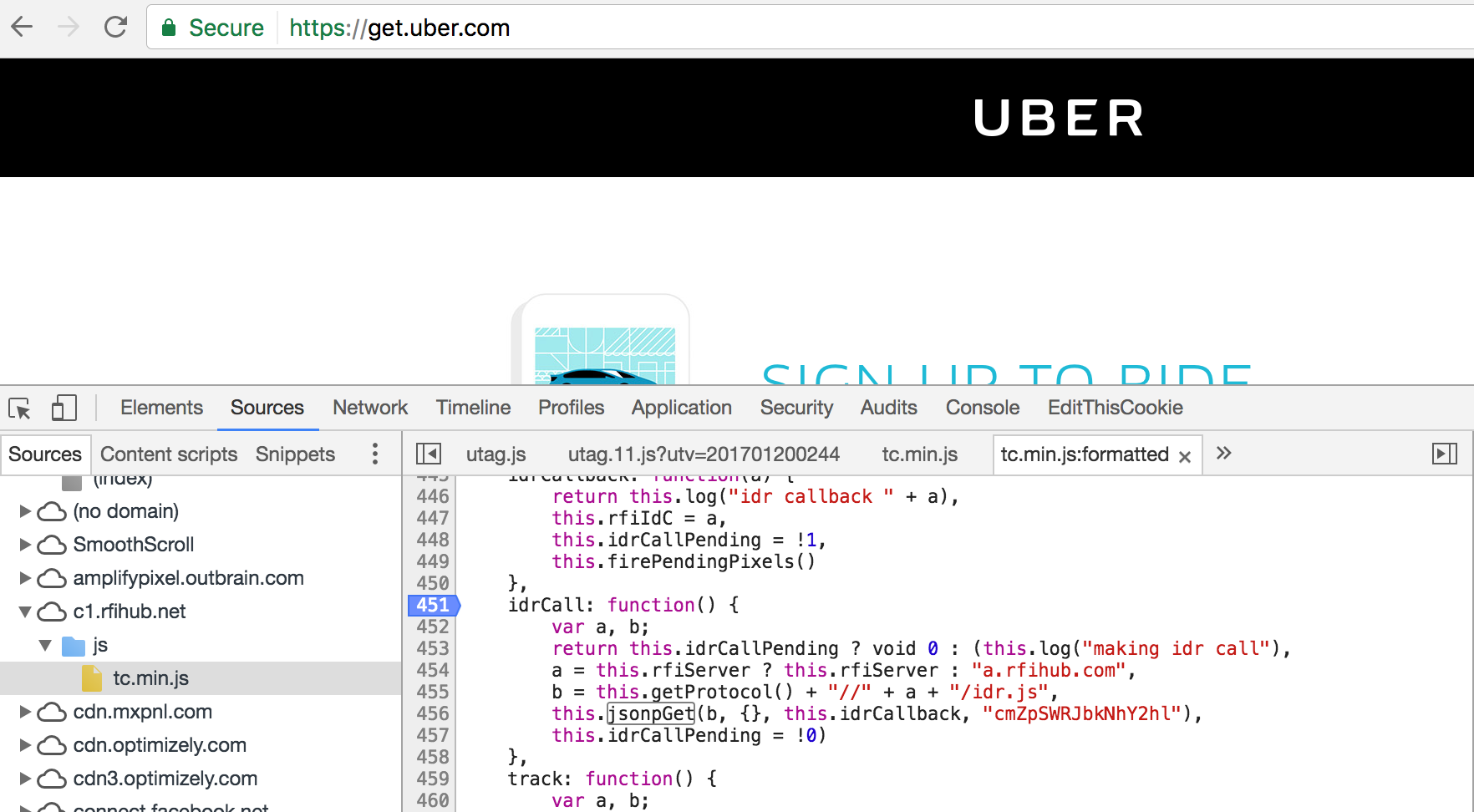
- Almost all of Uber’s websites are loading JS file: https://tags.tiqcdn.com/utag/uber/main/prod/utag.js
- I found that the content of utag.js is updating from
/data/utui/data/accounts/uber/templates/main/utag.jswhen deploying in my.tealiumiq.com. - my.tealiumiq.com has a path traversal issue, which allow hacker to change
utag.jsof other account, including Uber’s. - This bug had beed fixed 8 months ago. Bug Bounty: $6000.
My Steps
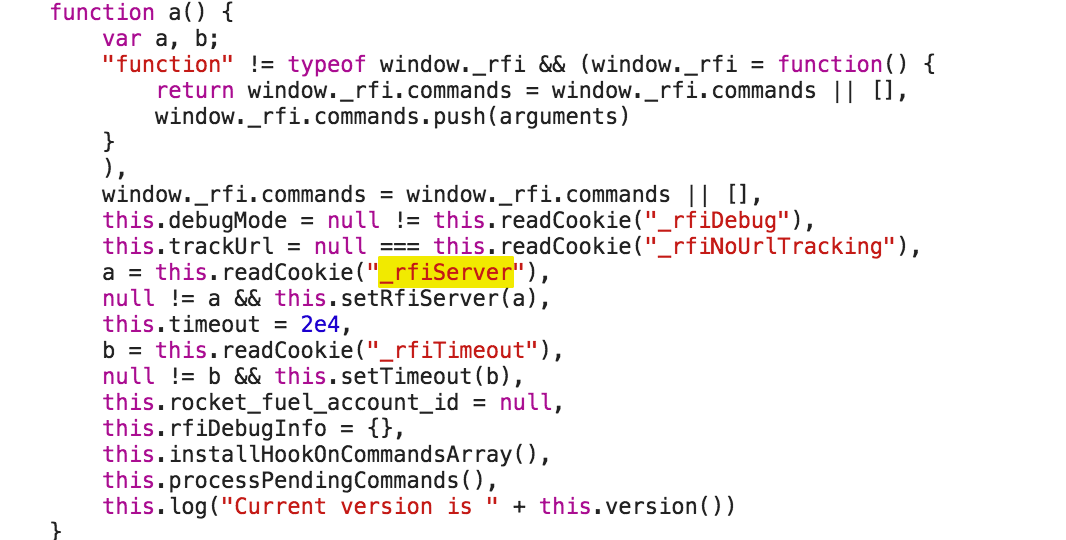
I like asking myself some questions when hunting for bug bounty. Looking around about https://tags.tiqcdn.com/utag/uber/main/prod/utag.js, I found Uber’s websites were using a third party service offered by Tealium. I asked myself: can I modify the content of utag.js? How?
I registered two account and began my journey. WARNING: DO NOT TEST IN PRODUCTION USING TARGET ACCOUNT.
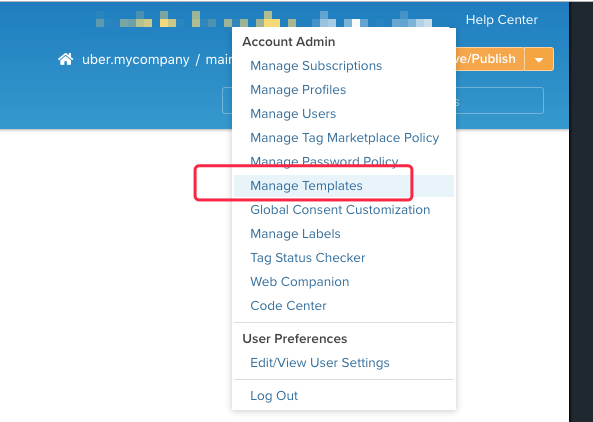
- Post
/urest/legacy/saveTemplatewithprofile=main%00to get the path in server
1 | POST /urest/legacy/saveTemplate?utk=044925f62222711fdfec11dc6a4e7160e053d31e1a7f4774e8 HTTP/1.1 |
Response
1
{ "message" : "There was an error updating this template: /data/utui/data/accounts/evilaccount/templates/main/utag.js"}
As you can see, the utag.loader template path is /data/utui/data/accounts/evilaccount/templates/main/utag.js
- Change the requst body to update the revision.loader
1 | POST /urest/legacy/saveTemplate?utk=688b137d1b8d8e884b3e1be4cd689843d0e3bc9705665f059b HTTP/1.1 |
Response
1
{ "message" : "There was an error updating this template: /data/utui/data/accounts/evilaccount/templates/main/201804081230/utag.js"}
As you can see 201804081230 is appearing at the path. After testing, I found that I can insert ../ into this path, which means that I can change utag.js of any account, including Uber’s.
1 | POST /urest/legacy/saveTemplate?utk=688b137d1b8d8e884b3e1be4cd689843d0e3bc9705665f059b HTTP/1.1 |